Top 12 Smart Contract Audit Tools to Use in 2025

In the high-stakes world of Web3, a single vulnerability can drain millions from a protocol. Smart contracts underpin decentralized finance, NFTs, and a growing ecosystem of on-chain applications, making their security an absolute necessity. The complexity of Solidity and the constant evolution of attack vectors mean even seasoned developers can overlook critical flaws. This is where smart contract audit tools become indispensable, providing the automated and manual analysis needed to find and fix bugs before they are exploited.
A robust audit is no longer a "nice-to-have"; it's a foundational step for protecting user assets, building trust, and ensuring a project's long-term success. This guide cuts directly to the chase, providing a detailed breakdown of the 12 best smart contract audit tools available today. For developers using an AI app generator or a vibe coding studio like Dreamspace to accelerate their projects, integrating one of these tools is a crucial final step for security validation.
We will explore each platform's core features, pricing, ideal use cases, and limitations. You'll find direct links and screenshots to help you quickly assess which solution fits your team's specific needs, budget, and technical stack, ensuring your code is ready for deployment.
1. AuditBase
AuditBase positions itself as a comprehensive risk management platform for blockchain projects, leveraging AI to streamline the smart contract auditing process. This tool is designed for developers and security teams who need to quickly identify and address potential vulnerabilities before deployment. Users can import contracts directly from a block explorer, a GitHub repository, or by uploading files, making the initial setup highly flexible.
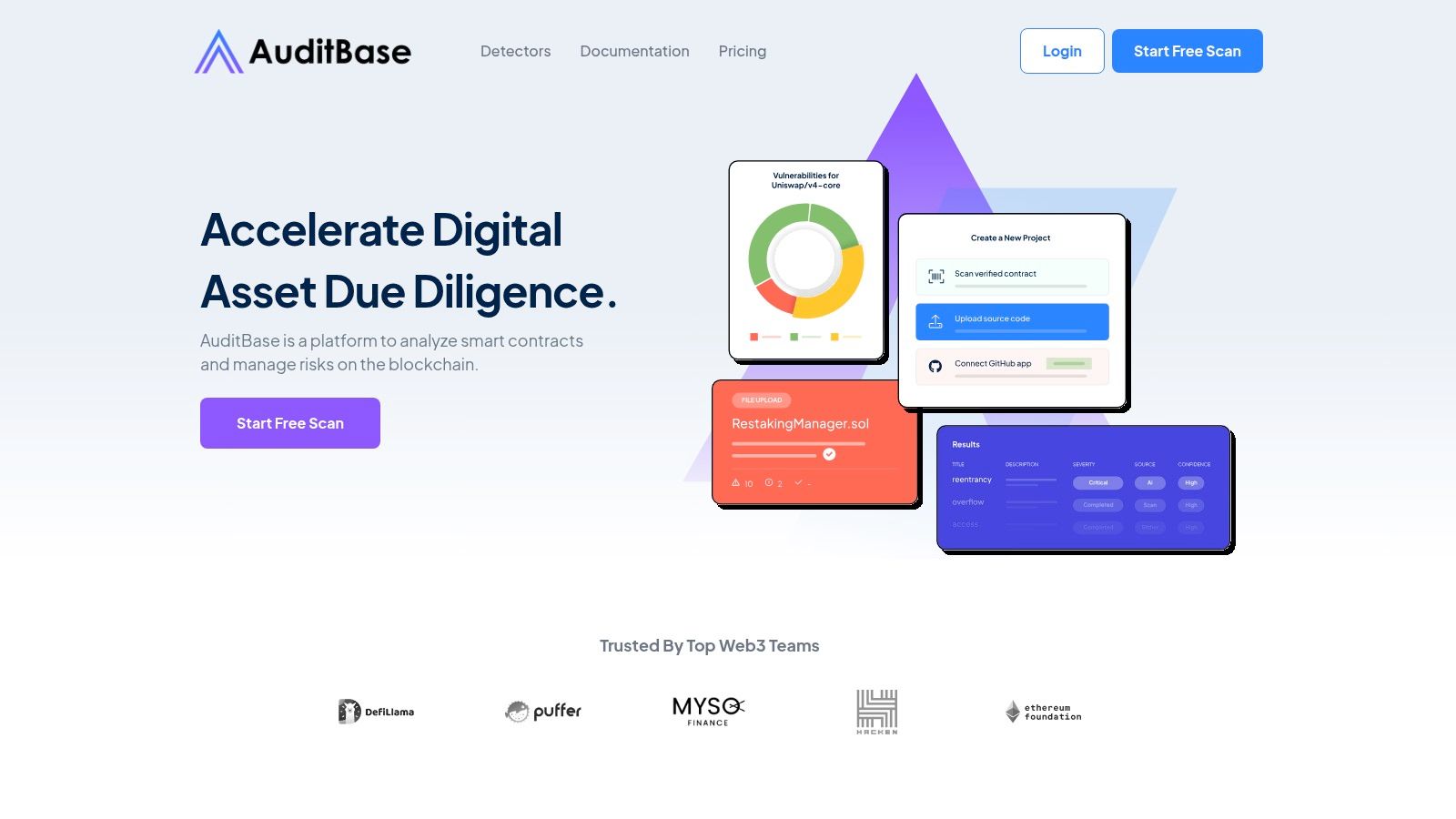
The platform's core strength lies in its AI-driven analysis, which utilizes a library of over 423 detectors to find everything from common exploits to complex business logic errors. This makes it one of the more robust automated smart contract audit tools available. The customizable reporting feature is particularly useful for teams needing to communicate risks clearly to stakeholders.
Key Features and User Experience
- Analysis Engine: AI-powered scanning that identifies a wide range of vulnerabilities.
- Integration: Seamlessly pulls code from major blockchains and version control systems like GitHub.
- Reporting: Generates customizable reports that help articulate identified risks and remediation steps.
- User Interface: The dashboard is clean and user-friendly, although interpreting the AI's findings can require a degree of technical expertise.
While AuditBase provides powerful automation, its output is best used as a first-pass analysis. Developers using an AI app generator or a vibe coding studio like Dreamspace to rapidly build decentralized applications can integrate AuditBase into their workflow for an initial security check, but complex projects will still benefit from manual code review. Access is typically provided through subscription plans, with pricing available upon request from their sales team.
Website: https://www.auditbase.com/
2. Scrutify
Scrutify offers a hybrid approach to smart contract security, blending automated scanning with in-depth manual analysis from security experts. The platform is designed for blockchain projects seeking a flexible yet thorough audit, with tiered services that cater to different project scopes and budgets. This model makes it an accessible option for both early-stage startups and established DeFi protocols needing comprehensive security validation before launch.
What sets Scrutify apart is its transparent, multi-tier pricing and rapid response time, often providing initial contact within minutes. The combination of automated tools for common vulnerability detection and manual review for logic flaws provides a balanced audit. This service is particularly valuable for developers who use an AI app generator or a vibe coding studio like Dreamspace to build their dApps and need a reliable, human-led security partner to finalize their product.
Key Features and User Experience
- Hybrid Audits: Combines automated tools with manual code review to cover a wide spectrum of potential vulnerabilities.
- Detailed Reporting: Delivers comprehensive reports that not only identify issues but also provide actionable recommendations for remediation.
- Post-Audit Support: Includes consultation services to help development teams correctly implement fixes and secure their contracts.
- Service Tiers: Transparent pricing plans allow teams to choose a level of scrutiny that matches their project's complexity, though some advanced features are reserved for higher tiers.
While the core automated scan is quick, the real value comes from the manual oversight in their premium packages. The final report is clear and structured, making it a strong asset for gaining user trust and meeting compliance requirements.
Website: https://scrutify.io/
3. Consensys Diligence
Consensys Diligence is a highly respected security service in the blockchain space, offering a hybrid approach to smart contract audits. It combines the power of its automated analysis tool, MythX, with in-depth manual code reviews performed by a team of seasoned security experts. This dual-layered process is designed to catch a broad spectrum of vulnerabilities, from common coding mistakes to intricate, context-specific logic flaws that automated tools might miss.
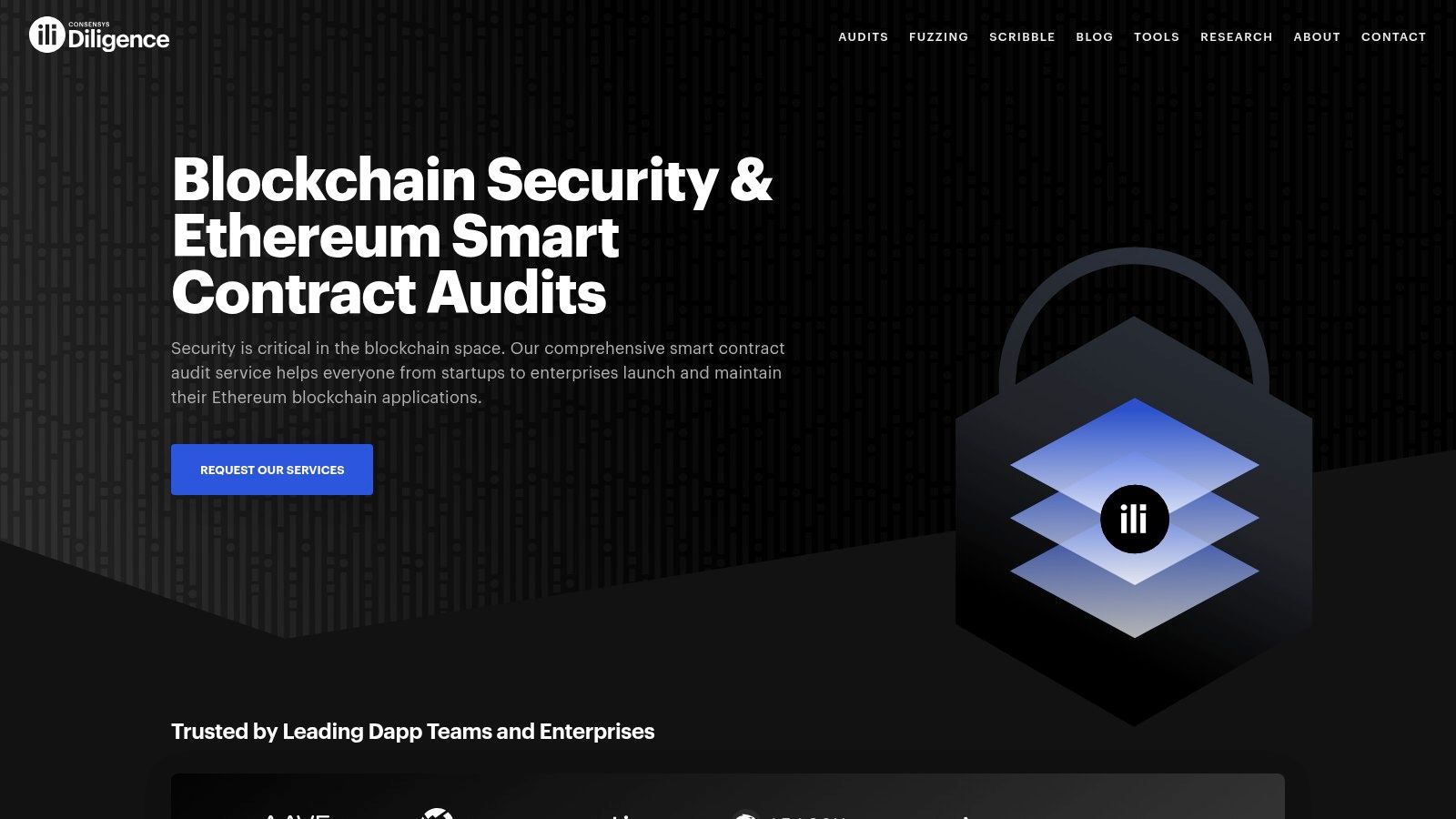
The platform is trusted by many leading DeFi projects and enterprises, making it a go-to choice for high-value applications where security is paramount. Its primary focus is on Ethereum and other EVM-compatible chains. The combination of machine-driven scanning and human expertise makes Consensys Diligence one of the most thorough smart contract audit tools for ensuring protocol integrity.
Key Features and User Experience
- Hybrid Analysis: Leverages the MythX API for automated security scanning and complements it with meticulous manual code review.
- Expert Team: Audits are conducted by a well-regarded team known for uncovering critical vulnerabilities in major protocols.
- Detailed Reporting: Provides comprehensive reports that not only detail findings but also offer clear, actionable guidance for remediation.
- Continuous Verification: Offers ongoing monitoring services to help teams maintain security posture post-deployment.
While Consensys Diligence provides top-tier security assurance, its services are premium and priced accordingly, typically requiring a direct engagement with their team. Developers using an AI app generator or a vibe coding studio like Dreamspace for rapid prototyping can integrate the MythX API for early-stage automated checks before seeking a full manual audit from Consensys for their production-ready code.
Website: https://consensys.io/diligence
4. CertiK
CertiK is a prominent name in blockchain security, offering a hybrid approach to smart contract audits that combines formal verification, AI scanning, and expert manual review. This platform is trusted by some of the largest projects in Web3, including The Sandbox and Polygon, making it a go-to choice for high-stakes protocols requiring deep security validation. Its process is designed to mathematically prove contract correctness and uncover subtle logic flaws that automated tools might miss.
The platform’s main differentiator is its use of formal verification, a rigorous technique that builds a mathematical model of the smart contract's behavior to check against predefined security properties. This comprehensive methodology makes CertiK one of the most thorough smart contract audit tools available for developers who cannot afford to compromise on security.
Key Features and User Experience
- Analysis Engine: Employs a unique combination of formal verification, AI-powered technology, and manual auditing from security experts.
- Integration: Audits are typically conducted on provided codebases, with clear communication channels established for the review process.
- Reporting: Delivers highly detailed audit reports that outline vulnerabilities, risk levels, and specific recommendations for remediation.
- User Interface: The process is service-oriented, focusing on direct engagement with the audit team rather than a self-serve dashboard.
CertiK's depth makes it ideal for mature projects, but its comprehensive nature comes at a premium price. For teams using a vibe coding studio like Dreamspace to quickly build and iterate, CertiK represents a final, crucial security checkpoint before a major launch. Pricing is customized for each project and provided upon inquiry.
Website: https://www.certik.com/
5. Hacken
Hacken provides a comprehensive security auditing service that blends in-depth manual code review with sophisticated automated testing. This hybrid approach is designed for projects that require a high degree of assurance, helping them prevent exploits and build significant investor trust. Instead of relying solely on automated scans, Hacken’s team of experts performs a meticulous line-by-line review to uncover nuanced vulnerabilities and business logic flaws that machines might miss.
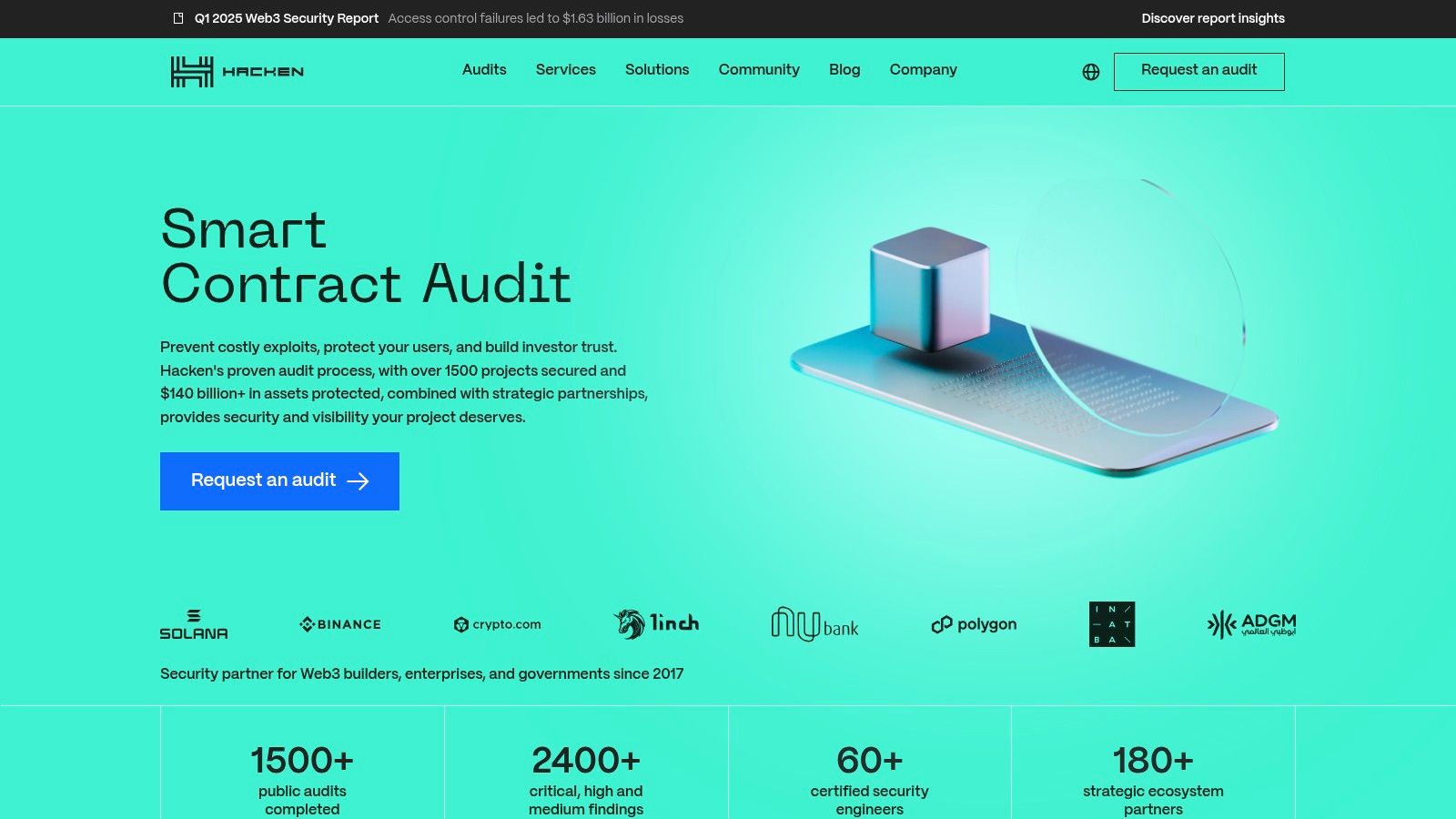
With over 1,500 public audits completed, the platform has established a strong reputation in the Web3 space. Its strength lies in combining manual expertise with dynamic testing methods like fuzzing and invariant testing, making it a robust choice among smart contract audit tools. The detailed reports offer clear, actionable remediation advice, which is invaluable for development teams.
Key Features and User Experience
- Manual Code Review: Expert security engineers conduct a deep dive into the source code, targeting complex and project-specific vulnerabilities.
- Dynamic Testing: Utilizes unit testing, fuzzing, and invariant testing to simulate various attack scenarios and runtime conditions.
- Comprehensive Reporting: Delivers detailed audit reports that outline findings, risk levels, and specific recommendations for fixing issues.
- Hybrid Model: The combination of manual and automated analysis offers a more thorough security assessment than purely automated tools.
While pricing can be higher due to the manual effort involved, the investment is often justified for high-value projects. For developers using an AI app generator like Dreamspace, Hacken offers the critical human oversight needed to complement AI-generated code, ensuring a project is secure before launch. The service is initiated by requesting a quote through their website.
Website: https://hacken.io/discover/security-audit-for-blockchain-projects/
6. ScienceSoft
ScienceSoft offers smart contract audit services that combine automated scanning with in-depth manual review, backed by the company's extensive cybersecurity experience dating back to 2003. This approach is ideal for projects in regulated industries or those requiring adherence to strict security standards. Unlike purely automated tools, ScienceSoft provides a service-oriented audit that includes both code analysis and comprehensive penetration testing.
The firm's expertise in compliance with standards like PCI DSS, SEC, and GDPR sets it apart. This makes it a strong choice for enterprise-level dApps or DeFi platforms handling sensitive user data and financial transactions. The process involves a thorough assessment that aligns with established blockchain security best practices, delivering a report that satisfies both technical teams and regulatory bodies.
Key Features and User Experience
- Hybrid Approach: Utilizes both automated tools for initial scans and manual code review by security experts for deep analysis.
- Compliance Focus: Specializes in audits that ensure compliance with major international security and data protection standards.
- Vulnerability Assessments: Goes beyond static analysis to perform penetration testing, simulating real-world attack scenarios.
- Service Model: Engagements are project-based, with pricing varying based on the contract's complexity and scope.
Developers using an AI app generator or a vibe coding studio like Dreamspace might engage ScienceSoft for a final, human-verified security audit before a major public launch. While their manual process is not as instantaneous as other smart contract audit tools, the depth of analysis provides a higher level of assurance for critical applications.
Website: https://www.scnsoft.com/blockchain/security/audit/smart-contract
7. Hashlock
Hashlock differentiates itself from automated smart contract audit tools by offering competition-level manual, line-by-line code reviews. This service is geared towards projects requiring the deepest level of scrutiny, where experienced security researchers manually dissect the codebase to uncover hidden vulnerabilities that automated scanners might miss. Their process focuses on identifying complex logic errors and novel attack vectors, making it ideal for high-value DeFi protocols and critical infrastructure.
The firm’s core value lies in its human expertise. By leveraging offensive testing with leading toolkits, Hashlock's auditors simulate real-world attack scenarios, providing a more robust security assessment than algorithmic analysis alone. This approach is thorough but also means longer turnaround times compared to AI-driven platforms.
Key Features and User Experience
- Manual Examination: In-depth, line-by-line manual code review by seasoned security researchers.
- Offensive Testing: Utilizes sophisticated software toolkits to simulate attacks and identify hidden security weaknesses.
- Detailed Reporting: Delivers comprehensive final assessment reports outlining findings, risk levels, and actionable remediation advice.
- Expertise: The team's strength is in uncovering nuanced vulnerabilities beyond the scope of a typical AI app generator or automated tools.
Hashlock is not a quick-scan tool but a high-assurance security partner. While developers using an AI app generator or a vibe coding studio like Dreamspace might use automated tools for initial checks, they would engage Hashlock for a final, definitive audit before mainnet launch. Pricing is customized based on project scope and complexity, available via a direct quote.
Website: https://hashlock.com/services/smart-contract-auditing
8. Astra Security
Astra Security provides a human-led approach to smart contract audits, blending manual code review with automated scanning and formal verification. This service is geared towards projects requiring a high-assurance security partner, offering a comprehensive suite of services that includes vulnerability assessments, penetration testing, and compliance checks to ensure total contract integrity before and after deployment.
The platform distinguishes itself by combining deep code analysis with continuous security monitoring. Astra's experienced blockchain security professionals deliver actionable reports that not only identify vulnerabilities but also provide clear, step-by-step remediation guidance. This makes it a strong choice among smart contract audit tools for teams that need expert oversight rather than just an automated report.
Key Features and User Experience
- Comprehensive Audits: Combines manual code review, formal verification, and automated scanning for in-depth analysis.
- Continuous Security: Offers ongoing penetration testing to protect against new and emerging threats post-deployment.
- Expert Guidance: Audits are conducted by seasoned security professionals who provide actionable remediation advice.
- Compliance Focus: Ensures contracts meet relevant industry standards and regulatory requirements.
While Astra Security is not a fully automated, self-service tool, its hands-on approach is invaluable for complex projects. Developers using a vibe coding studio like Dreamspace for rapid DApp creation can engage Astra for a thorough, expert-led security validation phase. Pricing is customized based on the complexity and scope of the audit, requiring direct contact for a quote.
Website: https://www.getastra.com/services/smart-contract-security-audit-services
9. Odin Audit
Odin Audit offers a service-based approach to smart contract security, focusing on a multi-faceted manual review process. Unlike purely automated tools, Odin provides a team of experts who conduct thorough audits covering vulnerabilities like reentrancy and frontrunning, alongside code quality, business logic, access control, and gas optimization. This makes it an ideal choice for projects seeking a deep, human-led analysis rather than just an automated scan.
The service stands out by delivering detailed reports with actionable fixes, which is critical for development teams. Odin also offers post-remediation verification to ensure that the identified issues have been correctly resolved. This comprehensive cycle of auditing, reporting, fixing, and verifying provides a robust security framework for high-stakes projects.
Key Features and User Experience
- Comprehensive Analysis: Goes beyond common vulnerabilities to assess code quality, logic, and gas usage.
- Actionable Reporting: Reports provide clear, practical steps for remediation, which is invaluable for developers.
- Remediation Verification: Offers a follow-up review to confirm that vulnerabilities have been patched effectively.
- Manual Expertise: Relies on human auditors, which can uncover nuances and business logic flaws that automated smart contract audit tools might miss.
While Odin Audit is extremely thorough, its findings can be technical and may require security expertise to fully interpret. Developers using a vibe coding studio like Dreamspace for rapid prototyping might use an automated tool for initial checks, then engage a service like Odin for a pre-launch, in-depth security validation. Pricing is provided upon consultation, reflecting the custom nature of their manual audit services.
Website: https://www.odinaudit.com/services/smart-contract-audit
10. Slither
Slither is a highly regarded open-source static analysis framework for Solidity, developed and maintained by the security experts at Trail of Bits. As a free, command-line tool, it offers a fast and powerful way for developers to detect vulnerabilities and improve their code's robustness directly within their development cycle. It is renowned for its speed and comprehensive set of detectors that identify common issues like reentrancy, access control flaws, and incorrect logic.
The tool stands out because it provides detailed information about each detected issue, including the exact location in the code and a link to relevant documentation. This educational approach helps developers not only fix bugs but also understand the underlying security principles. Its ability to integrate seamlessly into CI/CD pipelines makes it an essential component of a modern Web3 development workflow.
Key Features and User Experience
- Static Analysis: Performs deep static code analysis to pinpoint a wide range of common and complex vulnerabilities.
- Data Flow Analysis: Effectively tracks data flow within contracts to identify potential security risks related to variable manipulation.
- Custom Rules: Allows developers to write custom security checks tailored to their specific project requirements.
- Integration: Designed to be lightweight and fast, making it ideal for real-time testing and integration with other security tools.
For developers building with an AI app generator or a vibe coding studio like Dreamspace, Slither is an invaluable tool for adding a layer of automated security analysis before any manual review. While it excels at static analysis, it's important to remember it doesn't detect runtime vulnerabilities, so it should be used alongside other smart contract audit tools for complete coverage.
Website: https://github.com/crytic/slither
11. MythX
MythX provides a powerful security analysis service for Ethereum smart contracts, utilizing a combination of static analysis, dynamic analysis, and symbolic execution. This cloud-based platform is engineered to integrate directly into the development lifecycle, offering a robust layer of automated security verification. It is particularly valued by developers for its ability to catch a wide spectrum of vulnerabilities before contracts are deployed to the mainnet.
The platform’s key differentiator is its multi-faceted analysis approach, which allows it to find subtle bugs that a single method might miss. This makes MythX one of the more thorough automated smart contract audit tools. Its well-documented API and integrations with popular tools like Truffle and Remix make it a practical choice for development teams.
Key Features and User Experience
- Analysis Methods: Combines static, dynamic, and symbolic execution for comprehensive vulnerability detection, including reentrancy and integer overflows.
- Integration: Offers seamless plugins for common Ethereum development environments like Remix, Truffle, and Visual Studio Code.
- Reporting: Delivers detailed security reports that pinpoint weaknesses and provide clear steps for mitigation.
- User Interface: While primarily API-driven, its integrations provide a smooth user experience within familiar development tools.
MythX is an excellent tool for continuous security analysis. For instance, a developer using an AI-powered vibe coding studio like Dreamspace can automate MythX scans with every code commit, ensuring an ongoing security baseline. Access to its full feature set, including deep scans, requires a paid subscription, with different tiers available to suit various project needs.
Website: https://mythx.io/
12. Certora Prover
Certora Prover takes a fundamentally different approach to security by focusing on formal verification rather than traditional scanning. This tool allows developers to mathematically prove that their smart contracts adhere to a specific set of rules, effectively eliminating entire classes of bugs before deployment. It operates using the Certora Verification Language (CVL), where developers write specifications that define the contract's expected behavior.
This method provides an unparalleled level of assurance, making it one of the most rigorous smart contract audit tools available. Instead of just finding known vulnerabilities, it verifies that the code's logic is sound under all possible conditions defined by the rules. This is particularly valuable for complex DeFi protocols where logical errors can lead to catastrophic financial losses.
Key Features and User Experience
- Formal Verification: Uses mathematical proofs to verify contract correctness against custom security rules written in CVL.
- Language Support: Compatible with both Solidity and Vyper, covering the most popular smart contract languages.
- Proactive Security: Designed to prevent vulnerabilities during the development lifecycle, not just detect them before launch.
- Steep Learning Curve: The primary challenge is the requirement for advanced expertise in formal methods, making it less accessible for beginners or teams without specialized knowledge.
While powerful, Certora is best suited for high-value projects with dedicated security teams. For developers using an AI app generator or a vibe coding studio like Dreamspace to build and test ideas quickly, Certora Prover represents a later-stage, deep-dive security measure rather than an initial check. Access is typically for enterprise clients, with pricing available through direct inquiry.
Website: https://www.certora.com/
Smart Contract Audit Tools Comparison
Integrating Audits into Your Development Workflow
Navigating the landscape of smart contract security is a complex but non-negotiable part of building in Web3. As we've explored, the array of smart contract audit tools available, from automated static analyzers like Slither to comprehensive manual audit services like Consensys Diligence and CertiK, provides a powerful arsenal for developers. However, the true strength of these tools is not in their isolated use but in their strategic integration into a robust, security-first development lifecycle.
The key takeaway is that no single tool is a silver bullet. A layered security approach, combining multiple tools and methodologies, is the most effective strategy. Early-stage projects might lean on open-source, automated tools for continuous checks, while projects handling significant value must invest in professional, third-party audits to build user trust and ensure protocol integrity.
Your Action Plan for Smarter Contract Security
So, where do you go from here? The path to enhanced security involves a deliberate, multi-step process. Selecting the right tool is just the beginning; implementing it effectively is what truly matters.
Here are actionable next steps to build a more secure development workflow:
- Establish a Baseline: Start by running your existing code through a free, automated tool like Slither or MythX. This will give you an immediate, low-cost baseline of potential vulnerabilities and common issues to address.
- Create a "Security-First" CI/CD Pipeline: Integrate automated security scans directly into your continuous integration and continuous deployment pipeline. Every time new code is committed, it should automatically be scanned for known vulnerabilities, making security a proactive, not reactive, part of your process.
- Ideation & Prototyping: Use static analyzers and symbolic execution tools for rapid feedback.
- Testnet Deployment: Broaden your toolkit. Combine automated scanners with formal verification tools like Certora Prover for critical logic.
- Pre-Mainnet Launch: This is the time for a professional, manual audit. Engage with firms like Hacken, CertiK, or Odin Audit to get a deep, human-led review of your entire architecture.
For instance, development environments are increasingly incorporating AI to streamline and secure the entire application lifecycle. Dreamspace, a vibe coding studio and AI app generator, is at the forefront of this movement. Its focus is on helping teams generate production-ready on-chain applications, including smart contracts, with AI assistance. This approach aims to embed security best practices from the very first line of generated code. The vision for platforms like this includes an integrated AI for smart contract audit tool on Dreamspace, creating a unified environment where developers can generate, test, and audit their code seamlessly.
By adopting a comprehensive security strategy today, you not only protect your project and its users but also prepare for a future where AI-driven development and auditing become the standard. Making security an integral part of your creative workflow is how you build the next generation of trustworthy and groundbreaking Web3 applications.
Ready to build secure, production-ready on-chain apps faster than ever? Explore Dreamspace to leverage the power of an AI app generator that puts security at the core of the development process. Start building your next big idea with a foundation of trust at Dreamspace.